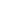In today’s world where mobile office and multi-device collaboration have become the norm, our phones, computers, and tablets store massive amounts of sensitive information: business contracts, customer data, financial records, personal communications, etc. This data is scattered across different devices, and once a device is lost, used by others, or subjected to unauthorized access, the risk of information leakage is almost immediate. Traditional device management methods either rely on manual deletion (which cannot ensure complete permission removal) or cloud synchronization (where data is stored on third-party servers, posing intrusion risks), neither of which fundamentally solves the problem of multi-device permission loss of control.
To address such risks, PlugOS provides three core security features: Product Key, Device Management List, and One-Time Setup Password. Together, they form a “permission protection network” to ensure that users can still precisely control which devices can access data and when to terminate access rights in multi-device collaboration scenarios.
I. Understanding PlugOS Security Core: Product Key
What is a Product Key?
The Product Key is the unique identity credential for a PlugOS device, similar to your “digital key” for your home. Each device corresponds to a unique key, usually provided in the form of a QR code card with the device packaging. This key is your only credential for accessing PlugOS and cannot be reissued if lost, so it must be kept safe.
Two Core Uses of the Key
The Product Key is only used for two high-security operations:
- Initial device binding: When using PlugOS on a new phone or computer, you need to scan the key’s QR code to complete identity verification and confirm the device binding.
- Factory reset: When you forget your unlock password, need to transfer the device, or suspect the key may be compromised, you must enter the Product Key to perform a factory reset.
Important Note: If you accidentally expose your key, you should immediately perform the “Reset Product Key” operation. After resetting, the old key will become permanently invalid and a new key will be generated, effectively preventing potential risks.
Three Key Principles for Protecting Your Key
To ensure key security, strictly follow these rules:
- Do not photograph the key QR code or save screenshots
- Do not transmit key information via WeChat, QQ, or other social software
- Do not discard the device packaging casually, as the key card is usually inside
II. Visual Device Management: Managing Host Devices
What is Host Device Management?
The Host Management feature serves as your “device access list,” where you can clearly see all bound devices, rename them, or remove device bindings that are no longer needed at any time. This feature gives you complete control over which devices can access your PlugOS.
Response Methods for Three Common Scenarios
Scenario 1: Only the phone is lost, PlugOS device is nearby
Core logic: The phone is just a “display carrier”; all core data is stored in PlugOS hardware. After losing your phone, you don’t need to worry excessively because:
- Anyone who finds the phone cannot launch the PlugOS client. Without a bound PlugOS device, it will only show “No device connected” and cannot even access the unlock interface.
- No PlugOS core data remains in the phone storage, so there’s no need to worry about data leakage.
New phone binding steps:
- Connect device and start binding
Connect your device to the new phone via USB, in the pop-up dialog:
- Check the “Always use” option
- Click the “Confirm” button
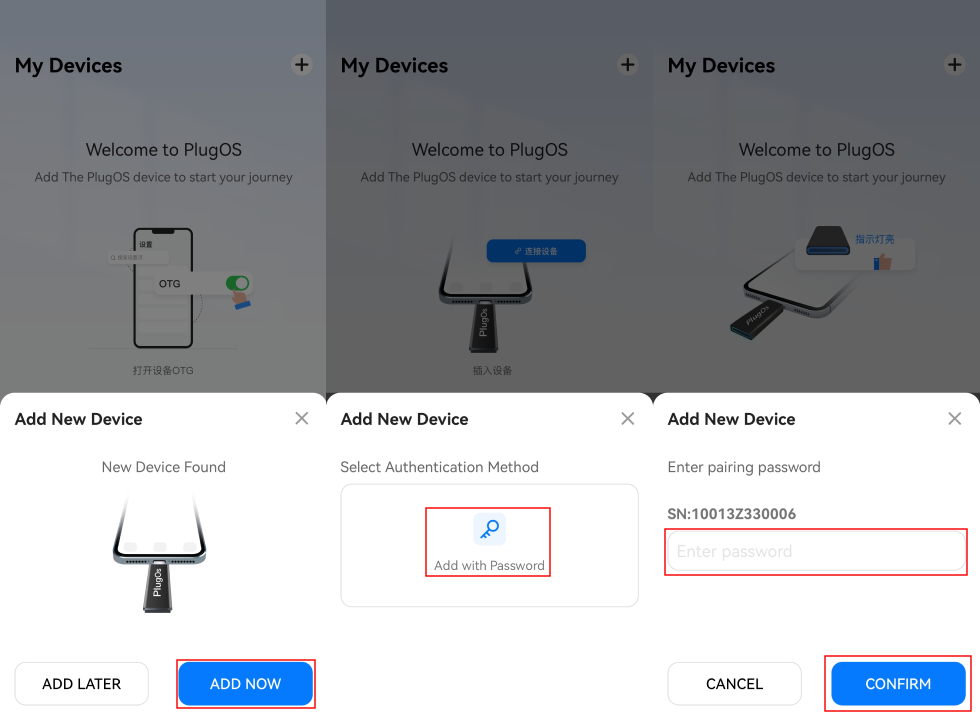
- The APP will automatically pop up a “New device found” window, click the “Add now” button to enter the binding process. Or “Add new device” to enter the binding process.
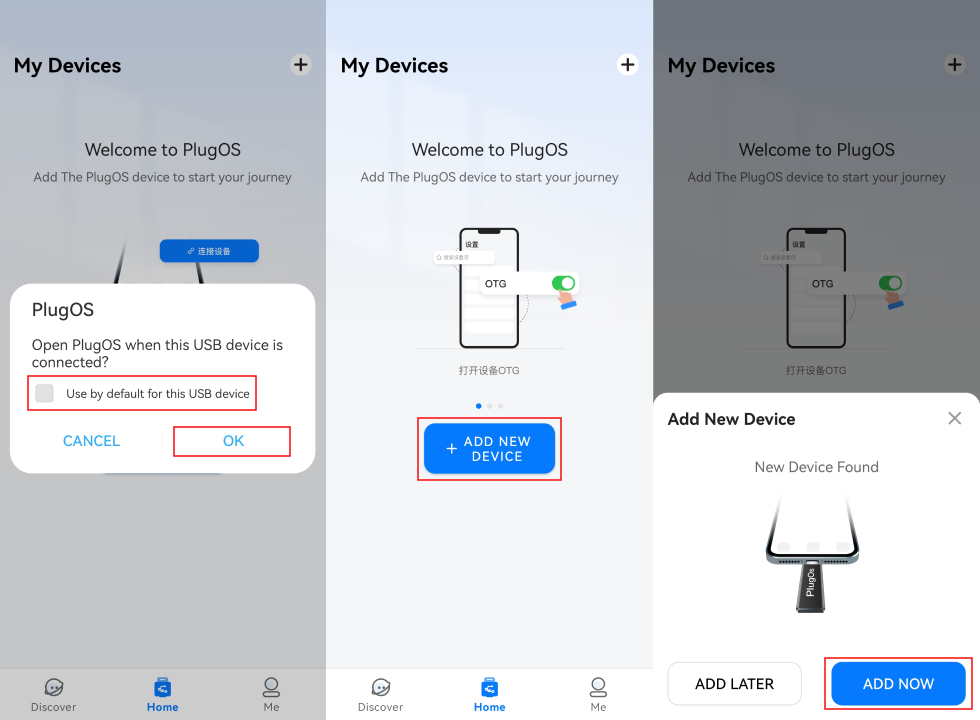
- Verify and complete binding
In the binding interface:
- Select the “Bind via Product Key” method
- Manually enter the product key or click the “Camera” icon to scan the product key QR code, then click the “Confirm” button to proceed to the next step
- Set a name for the device and click “Complete” to successfully bind.
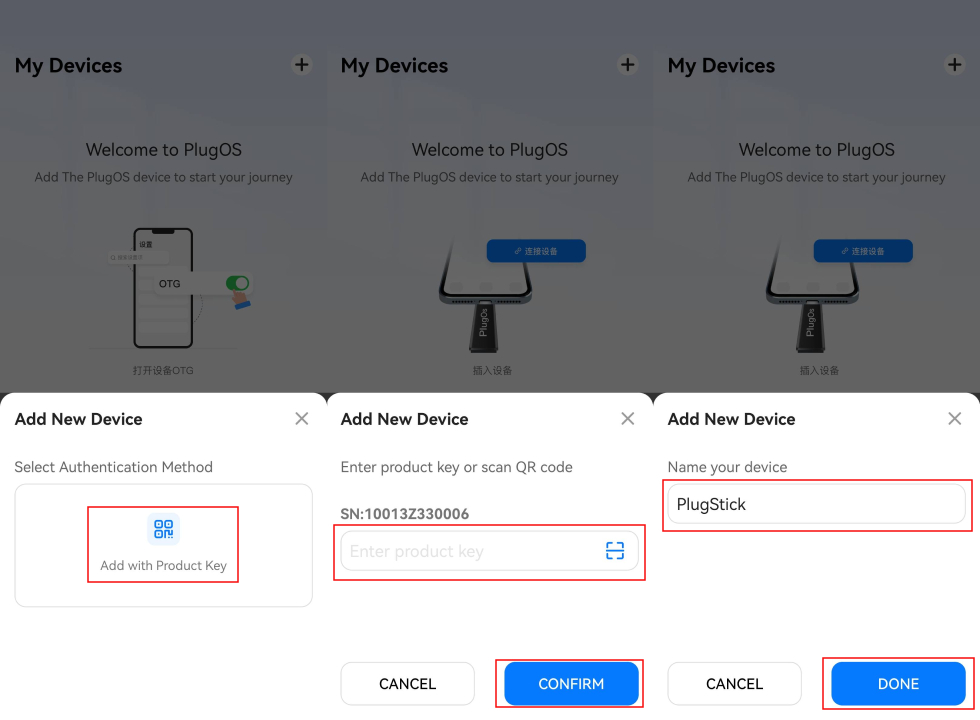
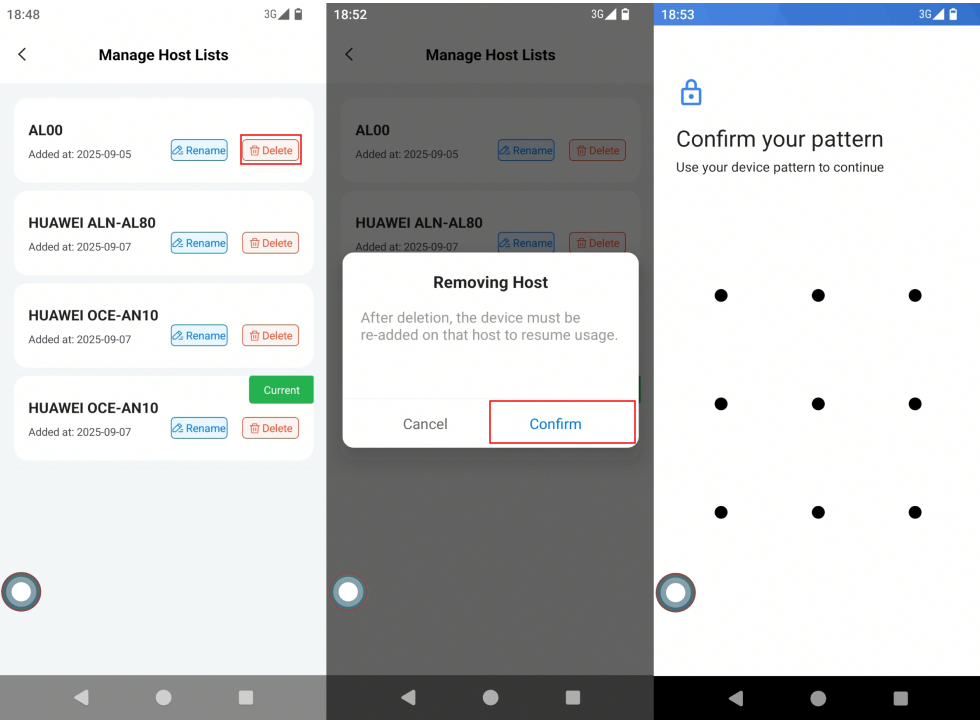
Steps to Remove Lost Device Binding:
- Enter device management Go to: PlugOS Settings → Device Authentication → Manage Authorized Devices.
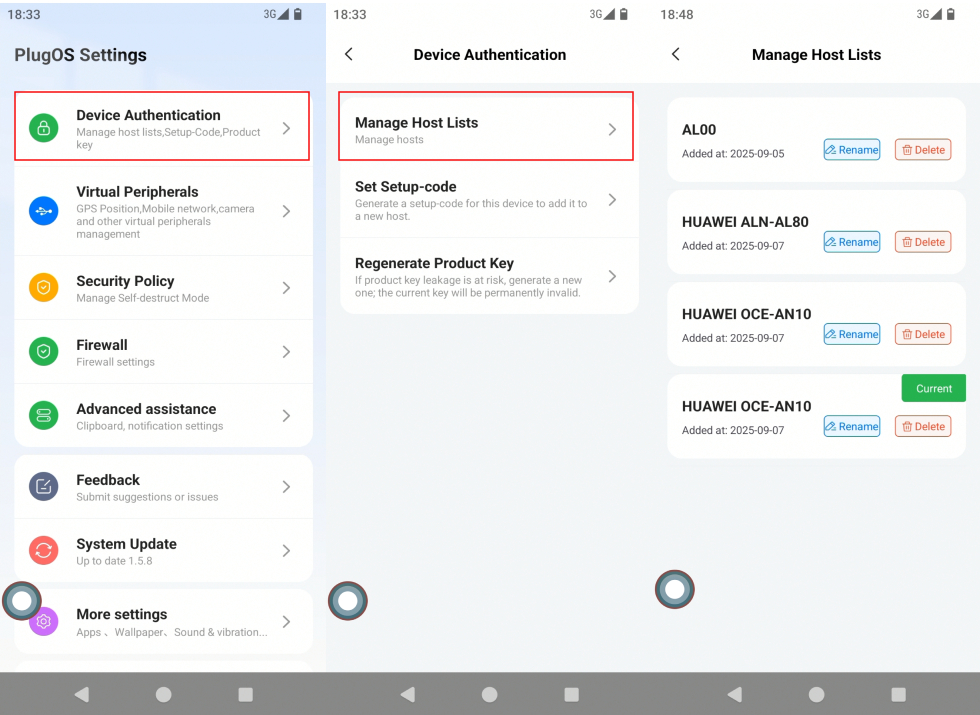
- Delete lost device
- Find the lost device to be unbound in the device list.
- Click the “Delete” button corresponding to that device.
- After the system pops up a confirmation dialog, click “Confirm deletion”.
- Enter the unlock password of the current device to complete verification and unbind.
Important Note: This operation will remove the device from your account, and the device will no longer be able to access related services afterwards.
Scenario 2: Only the PlugOS device is lost, phone is nearby
Core logic: PlugOS uses a “hardware + password” dual protection mechanism. Even if the device is lost, unauthorized persons cannot access your data:
- System cannot start without bound devices: PlugOS must be started through a bound device
- System cannot be accessed without password even with a device: The unlock password is stored in the hardware security chip and cannot be cracked
Important Note: All data is physically stored in the PlugOS hardware. After device loss, data cannot be recovered through bound devices or passwords.
Scenario 3: Too many devices to distinguish
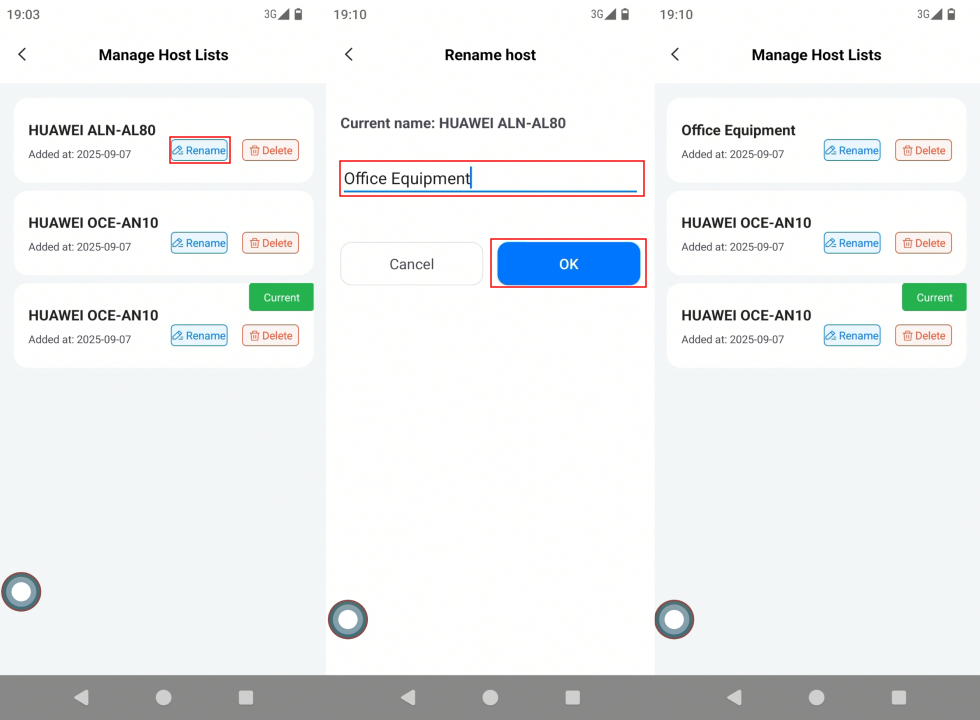
Solution: Use the rename function to add descriptive names to each device, such as “Company Computer - Finance Department” or “Personal Phone - Daily Use”, making device management clearer.
Steps to modify device name:
- Go to “PlugOS Settings” → “Device Authentication” → “Manage Host Devices”
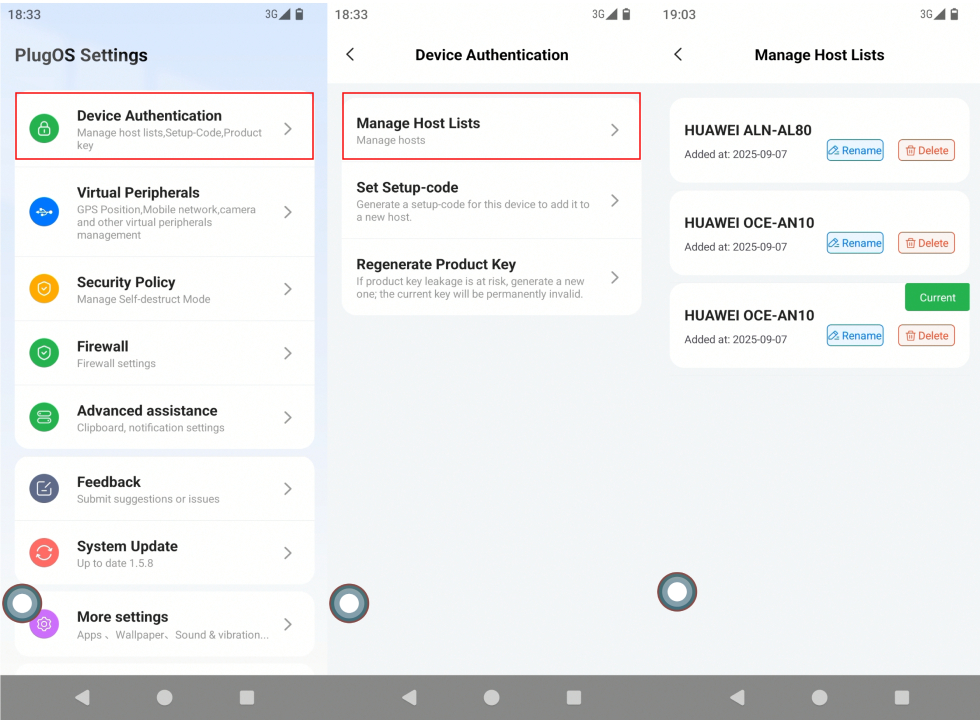
- Find the device to rename, click “Rename”, enter the new name, and click “Confirm” to save
III. Forgot to Bring Recovery Key? Use Temporary Setup Password to Bind New Device
Even if you’ve properly managed your device list, you might still encounter emergency situations where you’re away from home without your recovery key. In such cases, the Temporary Setup Password feature can help you securely bind new devices.
What is a One-Time Setup Password?
When you need to temporarily bind a new device (such as a hotel computer or borrowed phone) without your recovery key, you can generate a “One-Time Setup Password” through a bound device. This password has the following characteristics:
- Valid for 24 hours, automatically expires after that
- Only used for new device binding, no recovery key required
- Can be deleted from the device management list at any time after binding
Applicable Scenarios
- Need to temporarily access data using an unfamiliar computer during business trips
- Phone malfunction, need to use someone else’s phone in emergency
- Recovery key left at home, need to temporarily add a device
Steps to Generate and Use One-Time Setup Password:
- Enter the password generation page On a bound device, open PlugOS settings and go to: Device Authentication → Generate Setup Password. The system will pop up a confirmation dialog, click “Confirm”.
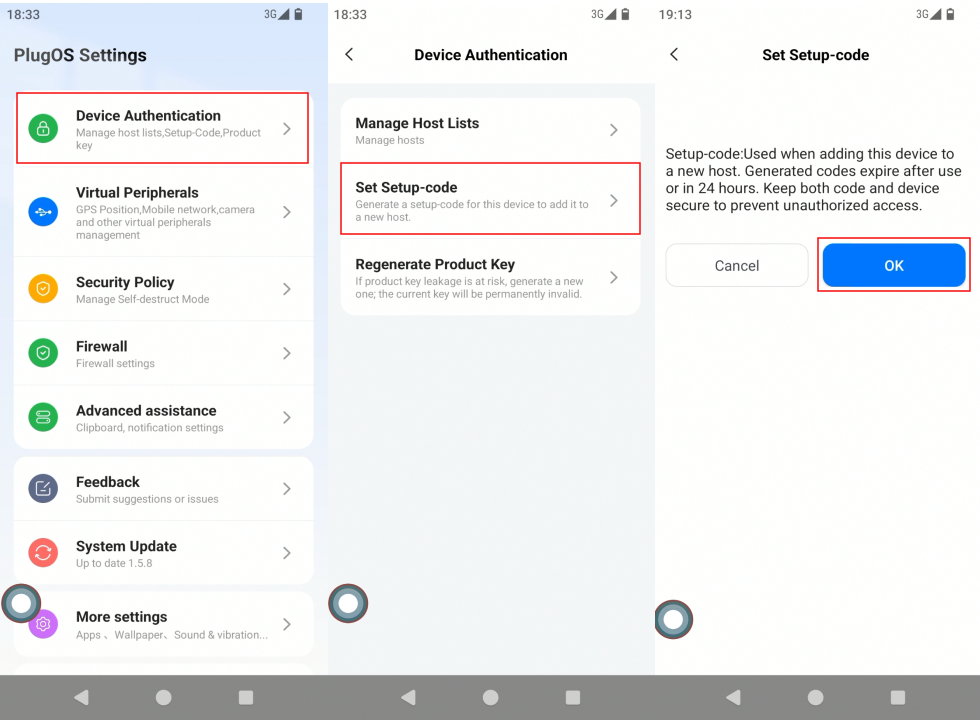
- Verify identity and generate password Enter the unlock password of the current device, and the system will generate an 8-digit temporary setup password. Remember the password, then click “Shut down now” (the system will pop up a confirmation dialog again, click “Confirm”).
Note: This password will automatically expire after use or 24 hours after creation. Password expiration does not remove existing binding relationships; manual deletion is required if needed.
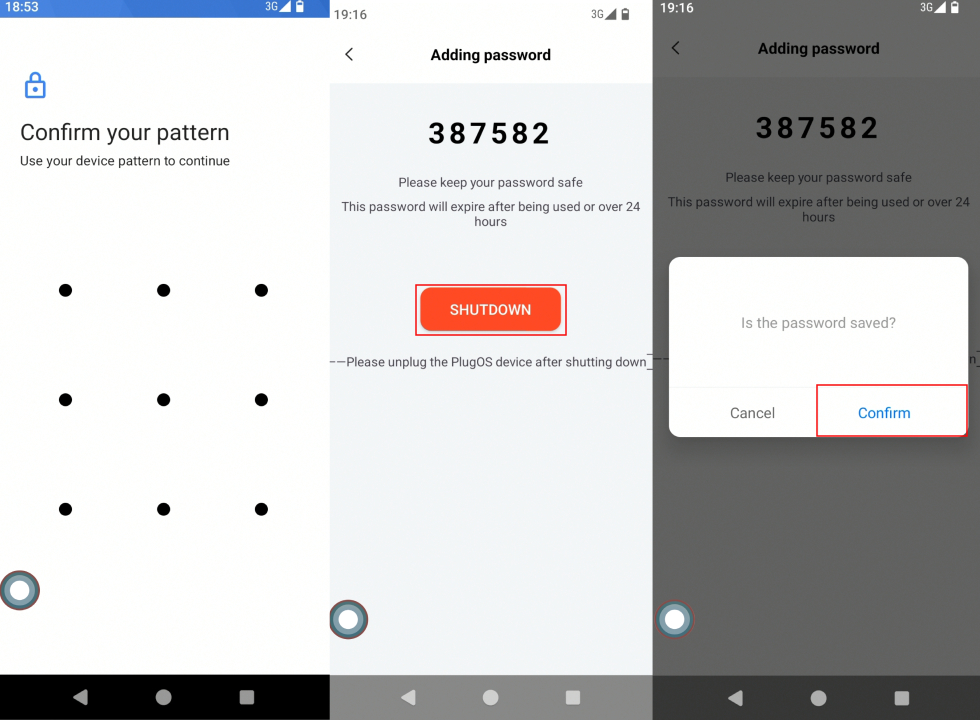
- Use password to bind new device Enter the above temporary setup password on the new device and follow the prompts to complete the binding process for the new device.
Security Recommendation: After generating the password, it is recommended to inform others verbally. Avoid transmitting it via text through SMS, WeChat, etc. to prevent leakage.
IV. Emergency Response to Key Exposure: Obtain New Product Key
Even with the above protective measures, keys might still be compromised due to accidents. In such cases, promptly obtaining a new product key is crucial to preventing risks.
Steps to Obtain New Key
- Enter the key acquisition interface Open PlugOS settings on the device and go to: Device Authentication → Obtain New Product Key to enter the new key application page.
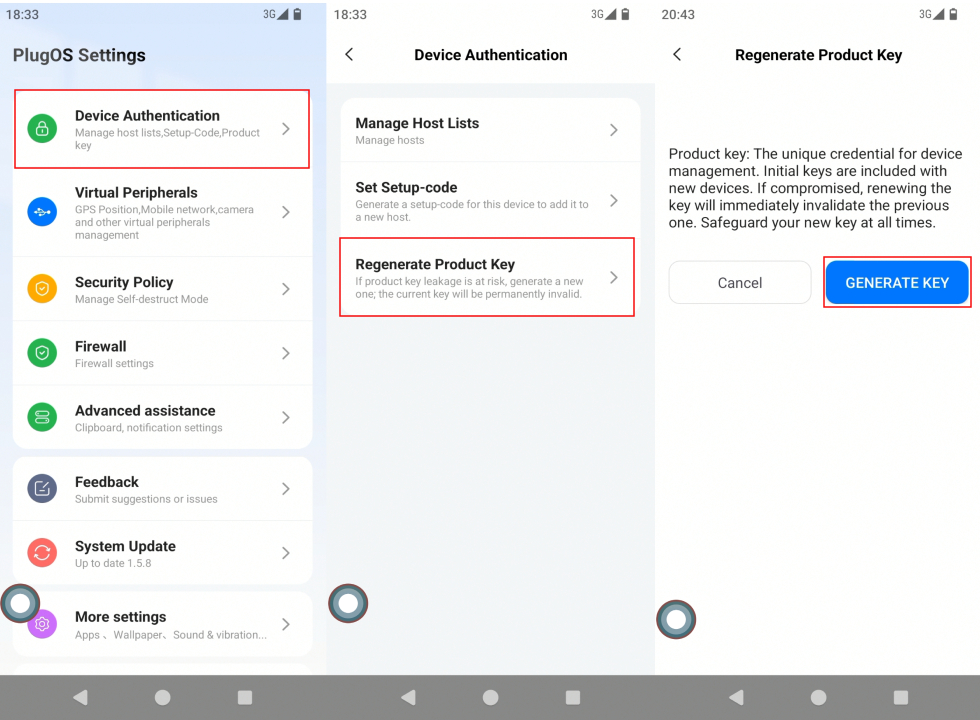
- Verify identity and generate new key Enter the unlock password of the current device to complete identity verification, and the system will generate a 16-digit new key. Be sure to save this key immediately, then click “Save to album or copy key only” to complete the reset.
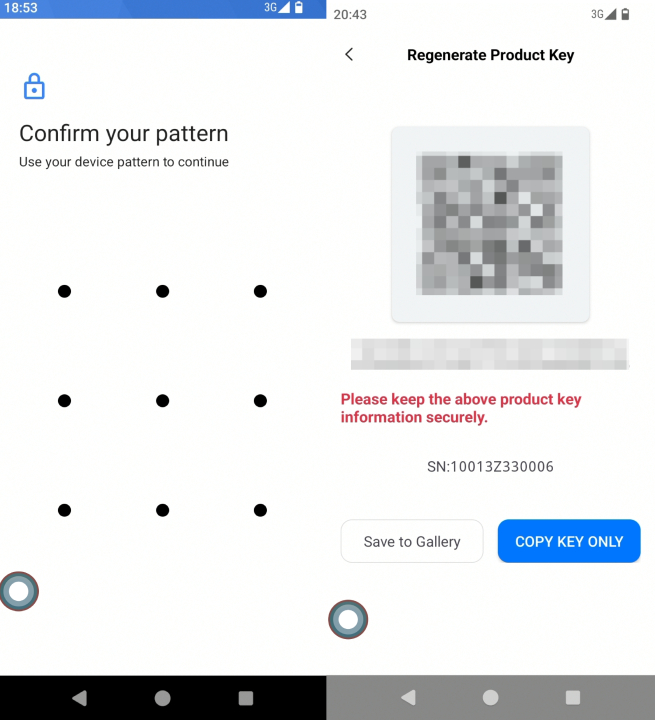
Two Important Steps After Reset
- Record the new key immediately: The system does not automatically back it up and it cannot be viewed again after closing the page
- Notify relevant personnel: If colleagues previously bound devices using the old key, inform them to use the new key for subsequent bindings
V. Extreme Scenarios with No Recovery
Even with all the above security measures, you need to be aware of the following extreme situations with no recovery options to take preventive measures in advance.
Scenario 1: PlugOS device lost and cannot be recovered
Core conclusion: All data is physically stored in the PlugOS hardware. After device loss, data cannot be recovered by any means, even if:
- You know the unlock password
- You have bound phones/computers
Preventive advice: Regularly export important files to external storage (such as USB drives or encrypted cloud storage) using the “Data Backup” function.
Scenario 2: Lost recovery key and no bound devices available
Core conclusion: When both of the following conditions are met, the device becomes permanently unusable:
- Lost Product Key
- All bound devices are lost/unavailable
Preventive advice:
- Bind PlugOS to at least 2 commonly used devices
- Store the key card in a safe place, not carried with the device
VI. Summary: Perfect Balance of Security and Convenience
The core of PlugOS multi-device security management system is giving complete control back to users. Through Product Key, Device Management List, Temporary Setup Password, and Key Reset functions, you can:
- Completely control device access permissions
- Securely share data without exposing core credentials
- Quickly take response measures when facing risks
Whether you need to manage multiple office devices or worry about security after device loss, PlugOS provides a simple, easy-to-use, and secure solution that allows you to enjoy the convenience of multi-device collaboration while ensuring data security.