
Independently developed Trusted Execution Environment (TEE) technology,
providing hardware-level security protection
Equipped with a self-developed Trusted Execution Environment (TEE), it builds a hardware-level safe box for sensitive data such as payment keys. Even if the system is compromised, it can still ensure that the core data remains as solid as a rock.

Hypervisor virtualization isolation technology
provides kernel-level protection
The breakthrough self-developed Hypervisor underlying isolation technology not only maintains full compatibility of applications but also firmly blocks virus and vulnerability attacks out of the sandbox.
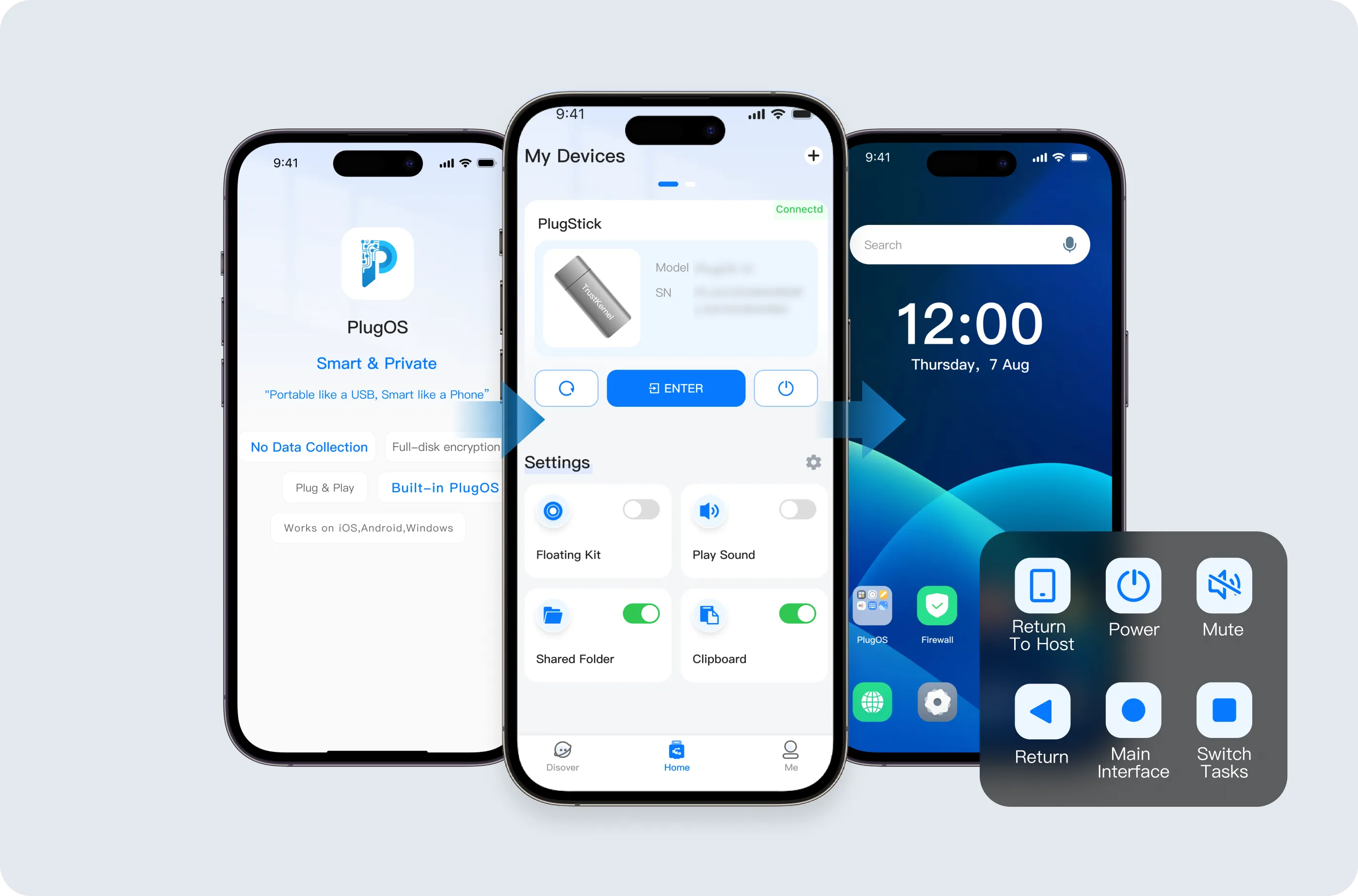
Full-cycle protection verification system,
Provide a financial-grade secure environment
From the hardware root of trust to the system kernel, step-by-step verification eliminates low-level attacks. Financial-grade security authentication is completed instantly upon startup, safeguarding the full-cycle security of the device from startup to shutdown

The dual-domain security engine effectively addresses the risk of data leakage when mobile devices are compromised
Running Android applications in an independent hardware environment and implementing full-link encryption not only addresses the risk of data leakage when mobile devices are compromised but also prevents applications from over-collecting private data。
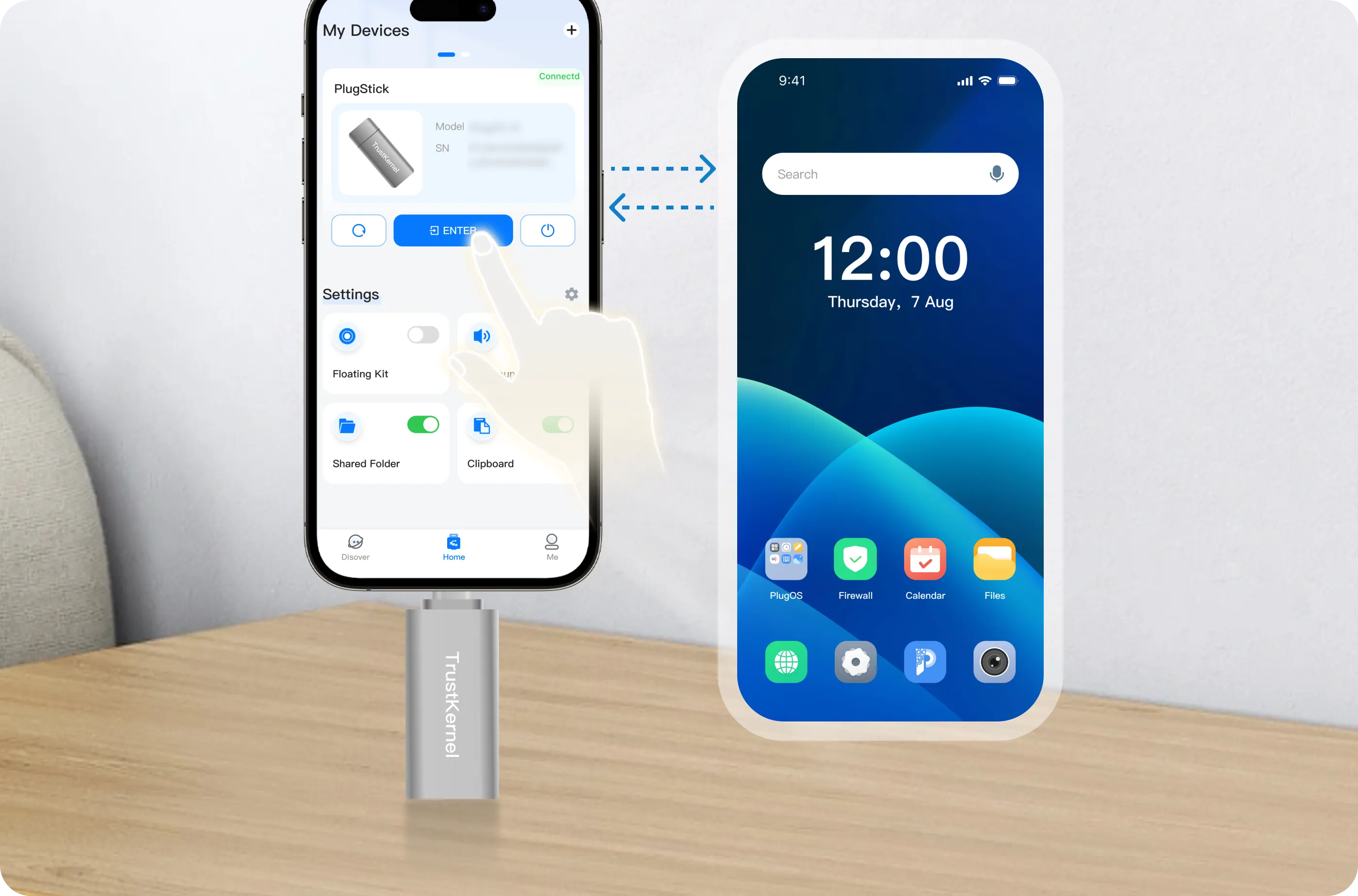
A USB flash drive-level ultra-micro system in size,
Empower full-stack mobile computing
It integrates a complete software and hardware system in the size of a USB flash drive. With efficient dynamic power consumption regulation technology, it provides high performance while being compatible with mainstream Android and Apple models.

Two-way secure handshake, zero-trust authentication
The device and the host are bidirectionally bound to ensure that illegal devices cannot impersonate legitimate identities through any means.

A privacy protection system for localized processing,
Zero data departure
Reconstruct the basic applications such as the photo album, input method, and browser, and remove the AD tracking code. Your browsing history, input content and other private information will always exist only locally on the device.